Set up Single Sign-On for 8x8 Admin Console
Single Sign-On(SSO) is an authentication service that allows users to access multiple applications using a single set of login credentials, such as their company username and password. Once authenticated, users can switch between authorized 8x8 applications without re-entering credentials.
Organizations that use identity management systems such as Google SSO, Microsoft Azure AD, Okta, mTIL or any SAML-compliant provider can configure SSO in 8x8 Admin Console. This enables employees to log in using their corporate identity rather than a separate 8x8 username and password.
With support for Federated SSO, users can securely log in to 8x8 applications through their company’s existing identity and security infrastructure.
Key features
-
Easy setup: Configure SSO directly from the user’s profile in 8x8 Admin Console.
-
Simplified access: Users no longer need to remember or enter separate 8x8, Inc. credentials.
-
Faster sign-in: Reduces login time across all 8x8, Inc. apps.
-
Enhanced security: Credentials are stored and managed only by the organization’s identity provider.
-
Seamless experience: Users can access 8x8, Inc. apps directly from other authenticated systems.
Identity Mapping
Each company user must be mapped to an 8x8 user account to enable federated authentication.
If your organization’s 8x8 usernames are not unique email addresses, configure one of the following identity attributes in 8x8 Admin Console:
- For SAML SSO: Use Federated ID.
- For Google SSO: Use Google ID.
This ensures proper identity matching between your organization’s identity provider and.
Configure Federated SSO
Configuring access to 8x8 applications through Federated Single Sign-On (SSO) involves setting up a SAML-based connection between your company’s identity provider and 8x8 Admin Console.
Security Assertion Markup Language (SAML) allows identity providers (IdP)to pass authorization credentials securely to service providers like 8x8, Inc..
SAML enables seamless authentication across systems without requiring users to log in multiple times.
Note: The SAML configuration process varies depending on your chosen identity provider. Contact your company administrator to confirm which IdP your organization uses. This step is typically managed by your IT or security team.
Provider-Specific Setup
Okta
- Search for 8x8 in the Okta Application Catalog and add it.
- Follow the SAML 2.0 setup instructions for 8x8 users whose Okta usernames match their 8x8 usernames.
- For users without matching usernames, the Federated ID field is populated in 8x8 Admin Console.
To learn more, see Configuring Okta SAML 2.0 SSO for 8x8 Admin Console.
OneLogin
- Search for 8x8 in the OneLogin Application Catalog.
- Under Configuration > Connectors, select Connector Version: SAML 2.0.
To learn more, see Configuring OneLogin SAML 2.0 SSO for Admin Console.
Azure AD
- Search for 8x8 in the Azure AD Enterprise App Gallery.
- Follow Microsoft’s configuration steps to connect your 8x8, Inc. service via SAML 2.0.
To learn more, see Azure (Entra) AD: 8x8 Single Sign-On (SSO) and User Provisioning (SCIM) Configuration.
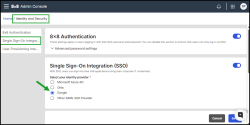
Administrators can set up Single Sign-On (SSO) and specify which identity provider (IdP) their organization uses to authenticate users.
To begin:
-
Go to Home > Identity and Security.
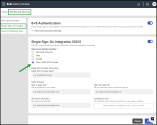
Switch on the Single Sign-On (SSO) toggle to enable the integration. -
Select your identity provider from the list — Google SSO, Azure, Okta, mTLS or Other SAML SSO Provider.
-
Follow the configuration steps for your chosen provider below.
Allows users to sign in to 8x8, Inc. applications using their Google ID.
To configure Google SSO:
- Go to Home > Identity and Security.
-
Select Single Sign on (SSO) as your authentication method.
- Choose Google as your SSO provider.
- Click Save.
Note: Users can choose to log in with either their 8x8, Inc. credentials or Google ID when both options are enabled.
Allows users to log in to any 8x8 application using their corporate Azure AD credentials.
To configure Microsoft Azure AD provider:
- Go to Home > Identity and Security.
- Select Single Sign on (SSO) as your authentication method.
- Select Microsoft Azure AD as your SSO provider.
-
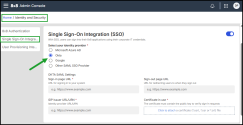
Enter the following details from your Identity Provider (IdP):
-
Sign-in page URL: The authentication URL provided by your IdP.
-
Sign-out page URL: The logout URL that ends the IdP session (to redirect users upon signing out).
- Append the
<{8x8Logout}>variable if your IdP can redirect after logout to insert the 8x8 login page, allowing the user to log in again later.
- Append the
-
IDP Issuer URL/URN: The identifier for your IdP (sometimes called IDP identifier URL/URN).
-
- .Upload the SAML signing certificate from Azure AD (Base64 format) under Certificate in use.
- Click Save to complete the configuration.
Allows users sign in to 8x8 applications .using their Okta Federated ID.
To configure Okta SSO:
- Go to Home > Identity and Security.
- Select Single Sign on (SSO) as your authentication method.
- Choose Okta as your SSO provider.
-
Enter the following information from your Okta configuration:
-
Sign-in page URL: The authentication URL from Okta.
-
Sign-out page URL: The logout URL that ends the IdP session (to redirect users upon signing out).
- Append the
<{8x8Logout}>variable if your IdP can redirect after logout to insert the 8x8 login page, allowing the user to log in again later. -
Example:
https://YOUR_COMPANY.okta.com/login/signout?fromURI={8x8Logout}
- Append the
-
IDP Issuer URL/URN: The Okta issuer identifier (sometimes called IDP identifier URL/URN).
-
-
Upload the SAML certificate file (.cert, .cer, or .crt) under Certificate in use.
- Save your changes.
Allows users sign in to 8x8 applications using Mutual Transport Layer Security (mTLS). This authentication option is available for 8x8 users accessing the service on Android devices.
Important! mTLS authentication is available only for customers using Multi-SSO integrations. To learn more about mTLS, see, Mutual Transport Layer Security authentication for Android devices.
Note: You can have only one mTLS identity provider at a time.
To enable mTLS SSO:
- Log in to 8x8 Admin Console.
- Navigate to Home > Identity & Security.
-
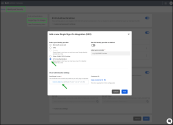
Under Single Sign-On (SSO), click + Add SSO.
-
In the Add a new Single Sign-On (SSO) integration dialog:
- Select mTLS Authentication as the identity provider.
- (Optional) Enable Set this provider as default, if applicable.
- Under Label your provider, enter a name for this SSO provider.
- Under MTLS Authentication settings, upload the root Certificate Authority (CA) in *.cert, *.cer, or *.crt format. Ensure the certificate contains the public key used for verifying sign-in requests.
- Copy the Customer ID for MDM configuration (used to match device certificates).
-
Click Add.
-
Click Save on the Identity & Security page.
Note: Only one mTLS identity provider can be configured per 8x8 account.
To learn more about multi-SSO integration and mTLS authentication, see Set up Multiple Single Sign-On for 8x8 Admin Console.
Supports any other SAML 2.0–compliant identity provider.
If your SAML provider requests an 8x8 URL, use: https://sso.8x8.com/saml2.
To configure Single Sign-On for other SAML SSO Provider:
- Go to Home > Identity and Security.
- Select Single Sign on (SSO) as your authentication method.
- ChooseOther SAML SSO Provider as your SSO provider.
-
Enter your IdP details:
-
Sign-in page URL: The login redirect from your IdP.
-
Sign-out page URL:The logout redirect from your IdP.
- You can append the
<{8x8Logout}>variable for return-to-login behavior
- You can append the
-
IDP Issuer URL/URN: The identifier for your IdP (sometimes called IDP identifier URL/URN).
-
-
Upload the SAML signing certificate under Certificate in use.
- Cick Save to complete your setup.
Configuration complete
Once configured, users can log in to 8x8 applications using their organization’s selected SSO provider.
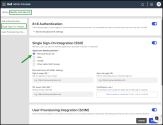
Admins can also enable User Provisioning Integration (SCIM) to automate user management.
For detailed setup guidance, see Set up User Provisioning Integration (SCIM).
This step is optional. If your company does not use unique email addresses for 8x8 usernames, then you must map 8x8 Work users to their Federation ID (for SAML) or Google ID (for Google) in the user records.
You have three options for adding/updating the Google ID/Federation ID in user records:
- Provide the Google ID/Federation ID in the CSV file during bulk user creation only.
- Provide the Google ID/Federation ID when a single user is created manually.
- Provide the Google ID/Federation ID when editing a single user manually.
To define Federation ID or Google ID in a user record:
- Go to Home > Users.
- Select a user record to edit. Based on the choice of the identity provider, the corresponding mapping field shows under Single Sign-On (SSO):
- For Okta and SAML, the Federated ID field is available. Populate the Federated ID.
- For Google, the Google ID field is available. Populate the Google ID.
- Save your changes.
You can also define Federated ID or Google ID while creating users in bulk.
To define Federation ID or Google ID while creating user records in bulk:
- Go to Home > Users.
- Click Bulk Upload.
- Download the advanced user template in the CSV format. The template opens in Excel.
- Look for columns User.FederationID and User.GoogleID, add the user data, and save the CSV file.
- Go to the Users page in 8x8 Admin Console. Click Bulk Upload.
- Drag and drop the CSV file and click Save.
Sign in Using Federated SSO
The sign-in process for 8x8 applications is similar whether it is authenticated via SAML or Google. The initial sign-in process takes users through the 8x8 Work login page. Go to the 8x8 SSO login page, or launch the 8x8 Work for Desktop.
- In the login screen, click Use Single Sign On.
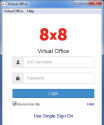
The SSO login prompt opens. - Enter your 8x8 username or company email for validation.
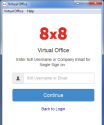
- Click Continue to view your SSO options.
- Click Log in using SAML to open your identity provider's login page.
OR
Click Log in using Google to open the Google login page.Note: Clicking Clear SSO Setting takes you back to the first login page.
- When prompted, click Allow to enable Adobe Flash Player settings to access your camera and/or microphone.
- If you selected Log in using SAML, your company's identity provider login page opens.
Note: If you log in using Okta or Centrify, the login page opens in a new browser tab instead of in the application window. Until you log in, the application window reads Login from browser....
- Enter the credentials to log in to the identity provider.
The 8x8 application launches.